Overview of the CMMC Program
The CMMC Program aligns with the department's existing information security requirements for the DIB. It is designed to enforce the protection of sensitive unclassified information shared by the department with its contractors and subcontractors. The program provides the DoW with increased assurance that contractors and subcontractors are meeting the cybersecurity requirements for nonfederal systems processing controlled unclassified information.
Key features of the CMMC Program:
Tiered Model: CMMC requires companies entrusted with sensitive unclassified DoW information to implement cybersecurity standards at progressively advanced levels, depending on the type and sensitivity of the information. The program also outlines the process for requiring protection of information flowed down to subcontractors.
Assessment Requirement: CMMC assessments allow the department to verify DIB implementation of existing cybersecurity standards.
Implementation through Contracts: DoW contractors and subcontractors handling sensitive unclassified information must achieve a specific CMMC level as a condition of contract award.
Protected Information
The CMMC model is designed to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) shared with defense contractors and subcontractors during contract performance.
Federal Contract Information (FCI): As defined in section 4.1901 of the Federal Acquisition Regulation (FAR), FCI is “information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government, excluding information provided by the Government to the public (such as that on public websites) or simple transactional information, such as that necessary to process payments.”
Controlled Unclassified Information (CUI): As outlined in Title 32 CFR 2002.4(h), CUI is “information the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that a law, regulation, or Government-wide policy requires or permits an agency to handle using safeguarding or dissemination controls.” For more information regarding specific CUI categories and subcategories, see the DoD CUI Registry website.
Overview of Assessments
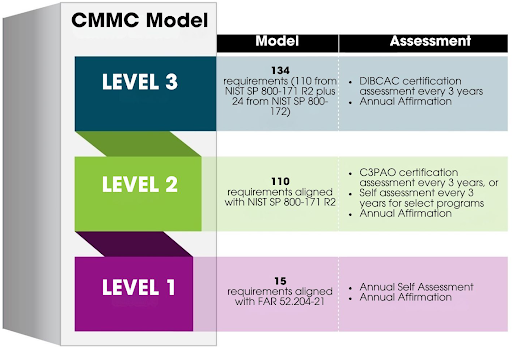
The CMMC Program provides assessments at three levels, each incorporating security requirements from existing regulations and guidelines.
Level 1: Basic Safeguarding of FCI
Requirements: Annual self-assessment and annual affirmation of compliance with the 15 security requirements in FAR clause 52.204-21.
Level 2: Broad Protection of CUI
Requirements:
Either a self-assessment or a C3PAO assessment every three years, as specified in the solicitation.
Decided by the type of information processed, transmitted, or stored on the contractor or subcontractor information systems.
Annual affirmation, verify compliance with the 110 security requirements in NIST SP 800-171 Revision 2.
Level 3: Higher-Level Protection of CUI Against Advanced Persistent Threats
Requirements:
Achieve CMMC Status of Final Level 2.
Undergo an assessment every three years by the Defense Contract Management Agency’s Defense Industrial Base Cybersecurity Assessment Center (DIBCAC).
Provide an annual affirmation verifying compliance with the 24 identified requirements from NIST SP 800-172.
| CMMC Status | Source & Number of Security Reqts. | Assessment Reqts. | Plan of Action & Milestones (POA&M) Reqts. | Affirmation Reqts. |
|---|---|---|---|---|
|
Level 1 (Self)
|
|
|
Not permitted |
|
|
Level 2 (C3PAO)
|
|
|
|
|
|
Level 3 (DIBCAC)
|
|
|
|
|
CMMC Post-Assessment Remediation: Plans of Actions and Milestones
The CMMC Program allows limited use of Plans of Action and Milestones (POA&Ms).
Level 1: POA&Ms are not permitted.
Level 2 and Level 3: Refer to §170.21 of the 32 CFR CMMC Program final rule for POA&M requirements, including critical requirements that cannot be included in a POA&M.
A POA&M closeout assessment is a CMMC assessment that evaluates only the NOT MET requirements identified in the initial assessment. The closing of a POA&M must be confirmed by a POA&M closeout assessment within 180 days of the Conditional CMMC Status Date. If the POA&M is not successfully closed out within this timeframe, the Conditional CMMC Status for the information system will expire.
Level 2 Self-Assessment: The POA&M closeout self-assessment shall be performed by the OSA in the same manner as the initial self-assessment.
Level 2 Certification Assessment: The POA&M closeout certification assessment must be performed by an authorized or accredited C3PAO.
Level 3 Certification Assessment: The POA&M closeout certification assessment will be performed by DCMA DIBCAC.
CMMC Implementation
The first phase of CMMC implementation will begin November 10, 2025. CMMC assessment requirements will be implemented using a four-phase plan over three years. The phases add CMMC Level requirements incrementally, starting with self-assessments in Phase 1, and ending with full implementation of program requirements in Phase 4. This phased approach allows time to train assessors and for companies to understand and implement CMMC assessment requirements.
In some procurements, DoD may implement CMMC requirements in advance of the planned phase
Frameworks & Controls
Access Control (AC)
Identification and Authentication (IA)
Media Protection (MP)
Physical Protection (PE)
System and Communications Protection (SC)
System and Information Integrity (SI)