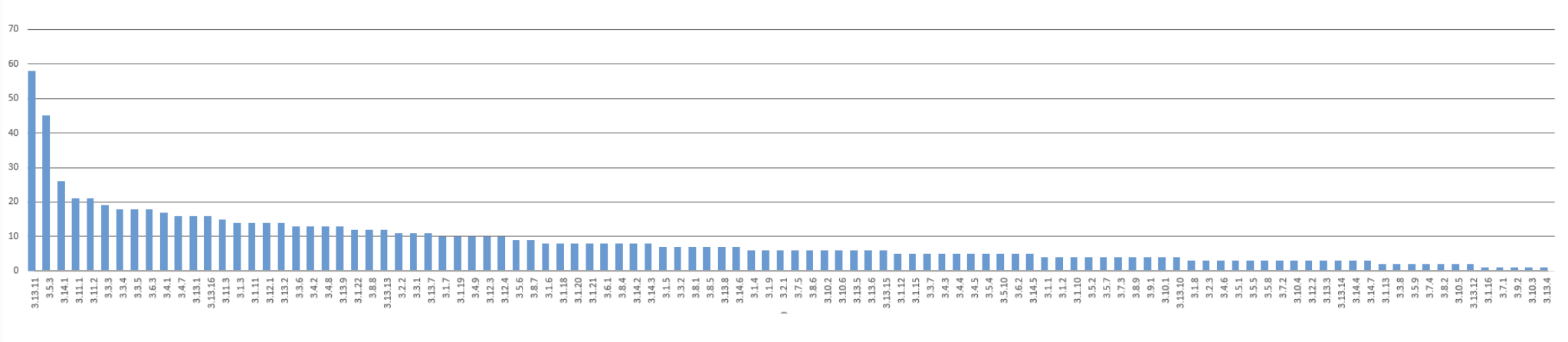
Most Commonly Failed Controls (DIBCAC Findings)
Top “Other Than Satisfied” Requirements
from DIBCAC High Assessments
The Defense Contract Management Agency (DCMA) conducted DIBCAC High Assessments between 2019–2022 to measure real-world adherence to NIST SP 800-171. The results revealed the most commonly failed requirements among contractors.
Presented By:
Defense Contract Management Agency (DCMA)
Defense Industrial Base Cybersecurity Assessment Center (DIBCAC)
December 2022
Top 10 Most Commonly Failed Controls
3.13.11, FIPS-validated cryptography [Systems and Communication Protection (SC)]
3.5.3, Multifactor Authentication [Identification and Authentication (IA)]
3.14.1, Identify, report, correct system flaws [System and Information Integrity (SI)]
3.11.1, Periodically assess risk [Risk Assessment (RA)]
3.11.2, Scan for vulnerabilities [Risk Assessment (RA)]
3.3.3, Review and update logged events [Audit and Accountability (AU)]
3.3.4, Audit logging process failure alerts [Audit and Accountability (AU)]
3.3.5, Audit record review, analysis, and reporting processes [Audit and Accountability (AU)]
3.6.3, Test incident response capability [Incident Response (IR)]
3.4.1, Establish/maintain baseline configuration [Configuration Management (CM)]
Percentage of Companies with Top 10 OTS Requirements
Data taken from 117 High Assessments (2019 – 2022) Total number of OTS = 883
| Topic | Website Link |
|---|---|
| DFARS Clause 252.204-7012, "Safeguarding Covered Defense Information and Cyber Incident Reporting" | https://www.acquisition.gov/dfars/part-252-solicitation-provisions-and-contract-clauses#DFARS-252-204-7012 |
| DFARS Cybersecurity FAQs | https://dodprocurementtoolbox.com/faqs/cybersecurity |
| NIST SP 800-171R2, "Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations" | https://csrc.nist.gov/publications/detail/sp/800-171/rev-2/final |
| NIST SP 800-171A, "Assessing Security Requirements for Controlled Unclassified Information" | https://csrc.nist.gov/publications/detail/sp/800-171a/final |
| NIST MEP CYBERSECURITY Self-Assessment Handbook for Assessing NIST SP 800-171 Security Requirements in Response to DFARS Cybersecurity Requirements | https://nist.gov/publications/nist-mep-cybersecurity-self-assessment-handbook-assessing-nist-sp-800-171-security |
| Supplier Performance Risk System (SPRS) | https://www.sprs.csd.disa.mil |
| DoD Assessment Methodology | https://www.acq.osd.mil/asda/dpc/cp/cyber/safeguarding.html#nistSP800171 |
Frameworks & Controls